800 800 070
Available H24
Via S. Pietro All’Orto 9, Milano
Via dei Gracchi 32, Roma
Via dei Gracchi 32, Roma
Email info@argocyber.it
Argo Cyber is a project with a high technological and specialized component unique of its kind.
Using advanced IT technologies, it identifies innovative and customized solutions for its customers.
Progressive digitalization, the increasingly stringent regulatory framework and the evolution of cyber threats bring out the need to implement or implement forecasting and treatment strategies that are adequate and proportionate to cyber-risks.
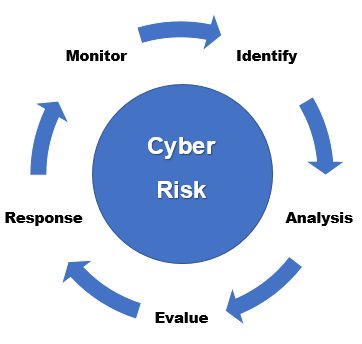
The Cyber Risk Assessment process is an integral part of any effective Cyber Security strategy, as it allows you to identify, monitor, assess and manage the risks and vulnerabilities of an IT system.
The identification of potential threats and vulnerabilities allows to prevent the occurrence of future security incidents and reduces exposure to possible cyber attacks that would undermine the confidentiality, reputation and production continuity of the organization with consequent economic losses.
The dynamic process requires constant monitoring of the estimate of the risk level in order to ensure the timely implementation of defense countermeasures and operational intervention plans suitable for their sector and organizational context.





The Vulnerability Assessment phase concerns the detection of existing vulnerabilities based on the results obtained during the Information Gathering phase. The data obtained through the first phase are analyzed on the basis of information disseminated on vulnerabilities. Diffusion guaranteed by accredited organizations such as Common Vulnerabilities and Exposures (CVE) and Open Source Vulnerability Data Base (OSVDB).
The analysis allows you to have an overview of the security level of the technological infrastructure, including standard applications and / or services, aimed at highlighting potential vulnerabilities. This phase mostly uses both open source and commercial automatic tools, such as IBM Rational AppScan, Acunetix, BurpSuite and scanners and scripts created ad hoc. An analysis of the results will then be conducted in order to identify and eliminate any false positives.
The aforementioned phase concerns the attempt to exploit any vulnerabilities detected in the previous phases. It is a typically manual activity conducted by highly specialized resources, and often performed with ad hoc developed software. The goal is to verify that there is no real possibility of exploiting the identified vulnerabilities and / or understanding the real impact of a potential system and data intrusion.
The following activity, thanks to the use of highly specialized resources, also leads to the discovery of new vulnerabilities, often more sophisticated and with greater criticality than those identified during the Vulnerability Assessment phase (it is estimated that 70% of new vulnerabilities found in this phase). Hence the great importance of the Penetration Testing activity carried out by highly specialized resources in order to give a more truthful view of the attack surface of a web application and thus avoid false senses of security due only to the use of software automatic scanning.
Available H24
Email info@argocyber.it

online and on-site payments with all the most common credit cards

Certified Investigation Agency for Quality System Management (ISO 9001) and Information Security Management (ISO 27001)
Protocol Investigation License No. 46633 / Area | TER O.S.P.
VAT 15137521009